Four Sovereignty Levels Any CIO Needs to Know
Making Europe Digitally Stronger by Demystifying Sovereign Cloud
As we’re moving more and more data to the public cloud, CIOs and CISOs are getting more concerned about what is happening with their data. How should they deal with this uncertainty? Enter Sovereign Cloud.
As mentioned in a previous article, there is no “the sovereign cloud”. Depending on who you ask, you get different definitions and methods. The objective, however, remains clear: sensitive data needs to remain protected from unlawful data extraction and processing.
To bring order to the chaos, we at Proximus NXT use a ‘map of the world’ to help IT decision-makers gain perspective. Workloads like apps and servers can run on various targets, each with their characteristics. For each target, we look at the following parameters:
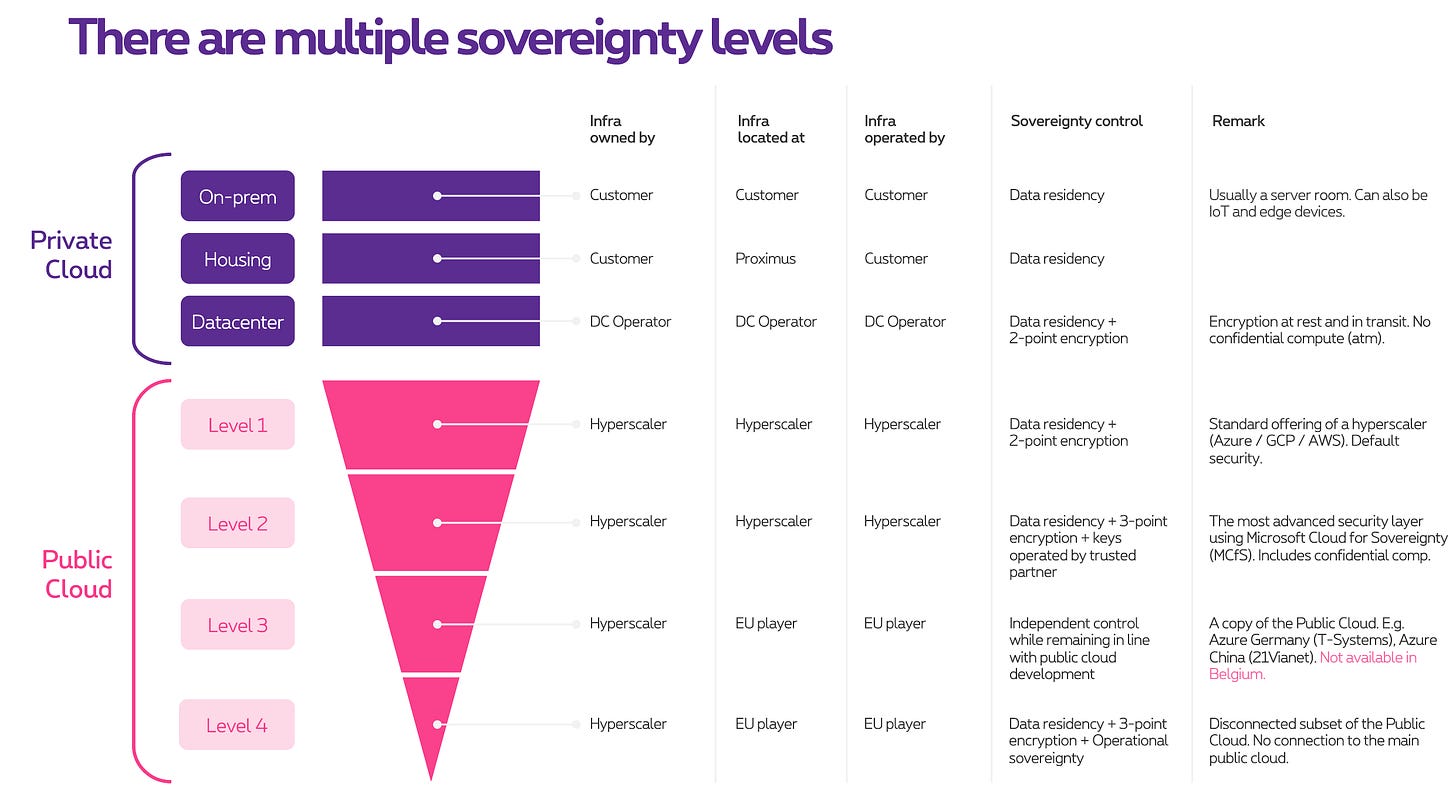
Who owns the infrastructure?
Where is the infrastructure located?
Who operates the infrastructure?
Which sovereignty controls are applied?
The Map of The World
The following image shows an overview of the various workload targets:
We see two broad categories: Private Cloud and Public Cloud.
Private Cloud: Tight Control
The classical offer of hosting workloads ranging from:
On-premise: The hardware is owned, located, and usually operated by you.
Housing: It’s your hardware but located at a private cloud provider. Ideal for those cases where you want to decommission your server room(s), but your hardware is still good for a few years.
3rd Party Datacenter: You lease computing, storage, and networking capabilities from a 3rd party that offers managed datacenter services.
The sovereignty controls in a private cloud are typically ‘data residency’ (your own premises or at a chosen provider, usually within your national borders) and ‘2-point encryption’ (encryption of data in transit and data at rest).
The big issue with Private Cloud is the lack of innovation compared to Public Cloud. Services like AI, emotion recognition, text-to-speech, big data analytics, and Machine Learning are almost exclusive to Public Cloud.
Private Cloud definitely has its value and benefits, but in reality, I find it’s stuck in the realm of IaaS (infrastructure).
Public Cloud: The Frontier of Innovation
So, where do you go for the innovation and scale? Yes, public cloud. The hyperscalers like AWS, Azure, and GCP thrive on making innovative services available to you.
We can classify the Public Cloud offering into four sovereignty levels:
Level 1
Regular Public Cloud. This is the standard offering and provides default security.
Sovereignty controls are ‘data locality’ (you choose the region) and ‘2-point encryption’ (encryption of data in transit and data at rest).
Level 2
The most advanced security layer. Requires confidential computing and other sovereign ingredients. For Microsoft Azure, this is MCfS (Microsoft Cloud for Sovereignty).
Sovereignty controls are ‘data locality’ (you choose the region) and ‘3-point encryption’ (encryption of data in transit + at rest + in use).
Level 3
A copy of the Public Cloud, but the cloud infra is located and operated by a national service provider. E.g. Azure Germany by T-systems, Azure China by 21Vianet.
The Public Cloud remains ‘on-fabric’, meaning it keeps receiving global updates like the regular public cloud.
Contains a subset of features of the regular Public Cloud.
Does not exist in Belgium / The Netherlands / Luxembourg.
Sovereignty controls are ‘data locality’ and ‘operational sovereignty’ (not the hyperscaler but a local service provider operates the cloud).
Level 4
Disconnected Cloud. Level 3, but where the hyperscaler has no connection to the cloud environment. E.g. GDCH (Google Distributed Cloud Hosting) in Luxembourg.
Contains a subset of features of the regular Public Cloud.
Sovereignty controls are ‘data locality’, ‘operational sovereignty’, and ‘3-point encryption’.
So what?
As a CIO or CISO looking to leverage the Public Cloud in a secure way, it’s important you understand the four sovereignty levels. Each level has its pros and cons, and careful consideration is required before deploying your workloads. If done well, you can benefit from the best of both worlds: the innovation of the Public Cloud with the information security of the Private Cloud.
Feel free to reach out if you have questions or comments!
Jetro WILS is the founder of BlueDragon Security, where he helps organizations operate safely in this cloud era by strengthening their digital security and compliance.