The Problem With Processing Sensitive Data in the Cloud
And How to Solve It
In a previous article, “What Is Confidential Compute and Why You Want It,” I discussed the importance of modern cloud security to use confidential computing.
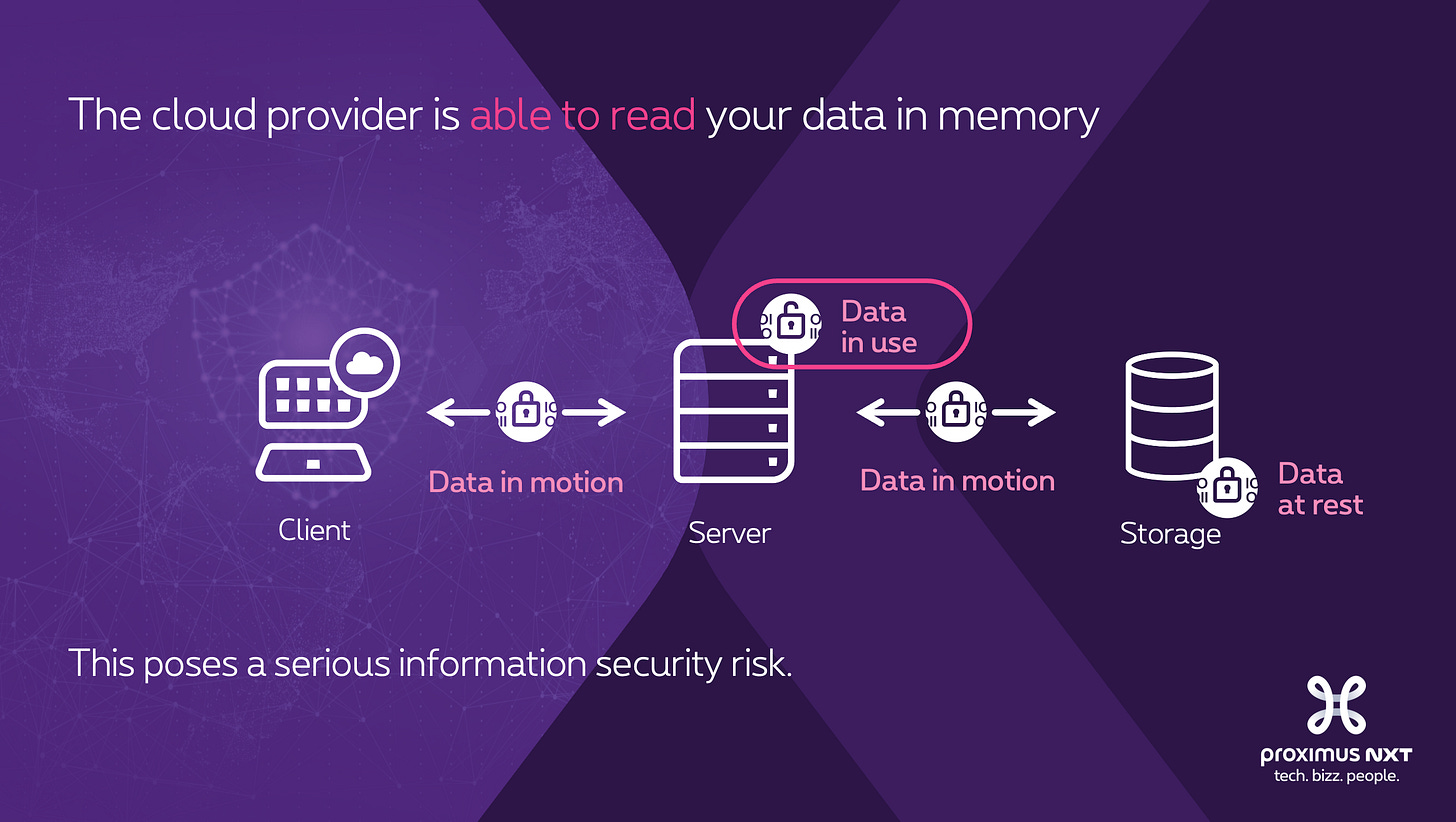
In essence, I stated that the cloud provider is able to read your data in memory because the data in memory lacks encryption. This applies to public, private cloud, and 3rd party datacenter providers. This poses a serious information security risk when the cloud hosts workloads with sensitive data.
What if I told you that, in reality, the risk is even greater?
An even greater risk
You see, your cloud workload doesn’t run in thin air. It runs on a stack of various hardware and software technologies. Here’s a simplified overview of a typical setup:
At the bottom of the stack, supporting all others, is the physical hardware. A bare-metal server with physical cables and physical hardware components.
The physical host runs an Operating System.
The Operating System usually runs a hypervisor that transforms the physical server into a virtualization platform. VMware and Hyper-V run on this layer.
The hypervisor hosts several virtual machines (VM).
Each VM has a guest Operating System.
Your VM app runs here. Or, in the case of containers, the Container Management platform (responsible for orchestration and runtime) like Kubernetes runs here.
Finally, your containerized app runs on Kubernetes nodes.
So while you interact with your app, it runs on a whole tech stack. If one layer fails, your app fails. If one layer has a security breach, your app is at risk.
Here’s the kicker: the data processed in memory is available to the lower levels of the tech stack. And thus, it’s available to all who have access to any level of the tech stack.
“All” means people, systems, and software.
“Access” means both physical and virtual.
Think of:
Administrators with physical or virtual access
Other tenants escaping their scope. A cloud platform is usually shared among different tenants (customers), and containers have thin walls.
Malware designed for memory exfiltration
For example: if the host OS on the physical machine gets infected with malware that sniffs the memory, it potentially has access to all data in use of all the layers above, including containerized apps.
As a cloud service consumer, you may think your app is running safely and securely while one of the lower levels is compromised.
And then, of course, there’s an insider threat, namely, admins having access to the systems. In information security, there’s a principle that says that if an attacker gains physical access to a device, it gets classified as a compromised system.
Confidential computing to the rescue
Right off the bat, I’ll say it very clearly: confidential computing doesn’t solve all threats but has a key role in protecting against in-memory breaches.
Confidential computing shuts down pathways of memory exfiltration by ensuring the data remains encrypted while the app is running in memory. The app runtime environment, with its memory footprint, becomes a black box for all layers underneath.
Confidential computing provides encryption on the silicon level so that the enclave in which the app runs, together with the allocated memory, is shielded from prying eyes:
Admins can no longer access the app’s memory
Fellow tenants on the shared platform escaping their scope cannot read the app’s memory
The malware-infected layers of the tech stack cannot read what’s going on in your app's memory
Confidential computing will become the norm
For roughly 15 years (1990-2005), we used the internet without encryption in transport (HTTP). Then, slowly transport layer security (TLS/SSL) became mainstream so that network communications are encrypted (HTTPS). These days you’re non-compliant if you use HTTP.
I often say to CIOs and CISOs that confidential computing is slowly becoming more mainstream, but it will be the norm in a few years. Just like our move from HTTP to HTTPS.
My recommendation: be ahead of the pack and use 2024 to learn more about confidential computing and sovereign cloud capabilities.
Jetro WILS is the founder of BlueDragon Security, where he helps organizations operate safely in this cloud era by strengthening their digital security and compliance.